|
We look at price, reach, perks and more to compare two of the biggest phone carriers in the US.
|
RELATED ARTICLES | | |
|
Google's Pixel 10A phone is now available for preorder, featuring a small feature refresh in a design that looks quite similar to last year's Pixel 9A.
|
|
We found the iPhone Air to have a pretty decent battery life for such a thin-and-light phone, somewhere in the region of 27 hours if you're continuously streaming video. But it's still a phone, arguably your most used device on a daily basis, so you may need to top it up during the day if you're using it constantly. That's where Apple's iPhone Air MagSafe battery pack comes in, and it's currently on sale for $79.
This accessory only works with the iPhone Air, but much like the phone it attaches to, it's extremely slim at 7.5mmm, so crucially doesn't add so much bulk when attached that it defeats the point of having a thin phone in the first place. The MagSafe Battery isn't enormous a
|
RELATED ARTICLES | | |
|
Rivian suggests that vehicle owners can leave their phone at home (or perhaps in a glove box) and instead control some aspects of their EV using a new Apple Watch app. With a tap of your watch, you can unlock and lock the doors, sound the alarm and vent the windows. After the digital key is set up, R1S and R1T Gen 2 owners can unlock their vehicle automatically simply by walking up to it thanks to the passive car key feature.
It's possible to set the cabin temperature and a target state of charge by turning the digital crown on an Apple Watch. You also can choose four quick controls to put front and center in the app and add a battery status indicator to your watch face if you so wish. Rivian says it will update its Apple Watch app with new features in the future.
Rivian first enabled digital car key support on Apple, Google Pixel and Samsung devices back in December. Apple started supporting digital car keys on
|
|
Now that pre-orders are open for the Google Pixel 10a, it's time to see how it stacks up against last year's Pixel 9a. At first glance, the two phones look very similar, and that's not a bad thing. Google hasn't tried to reinvent its budget-friendly formula this year, sticking to the same compact design, clean software experience and camera-first approach that made the 9a such a good value.
Both phones share a lot in common, including 120Hz OLED displays, Google's Tensor G4 chip, strong computational photography and seven years of OS and security updates. The actual differences are more incremental, including a moderately brighter, tougher display, improved Extreme Battery Saver longevity, slightly faster wireless charging and the addition of Satellite SOS. Importantly, Google is keeping the starting price the same as before, with both phones coming in at $499.
On paper, the Pixel 10a doesn't dramatically rethink what an affordable Pixel should be, but it does offer meaningful upgrades for the same price. While we wait for a review unit to evaluate the Pixel 10a's day-to-day performance, here's a quick comparison of the spec sheets of the two devices to see what the new model brings.
Pixel 10a vs Pixel 9a: Design and displayThere's very little separating these two on performance. Both the Pixel 9a and Pixel 10a run Google's Tensor G4 chip with 8GB of RAM and the same storage options, so day-to-day speed should feel virtually identical. The Pixel 10a ships with Android 16 out of the box, though the 9a can be updated to the same version.
Off the bat, the Pixel 10a doesn't look dramatically different from the Pixel 9a, and that appears to be intentional. Google is sticking with the same compact, no-frill
|
|
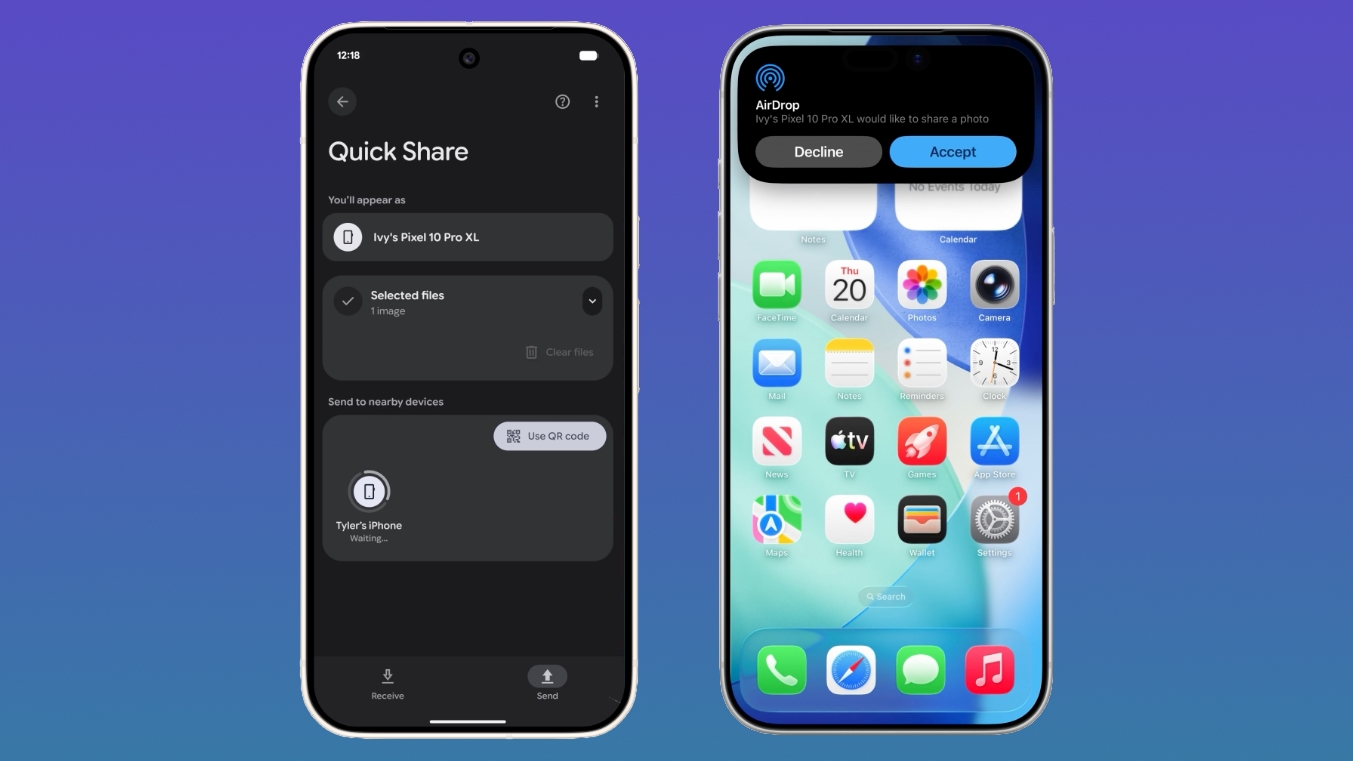 Google is expanding its cross-platform file sharing feature to additional Android devices, allowing them to transfer files to an iPhone using the AirDrop protocol. AirDrop support for Quick Share is coming to the Pixel 9, Pixel 9 Pro, Pixel 9 Pro XL, and Pixel 9 Pro Fold over the next few days. Google is expanding its cross-platform file sharing feature to additional Android devices, allowing them to transfer files to an iPhone using the AirDrop protocol. AirDrop support for Quick Share is coming to the Pixel 9, Pixel 9 Pro, Pixel 9 Pro XL, and Pixel 9 Pro Fold over the next few days.
|
|
 Amazon this week has a pair of discounts on a few AirPods models, including the AirPods 4 and AirPods Max. You can get the AirPods 4 for $99.00, down from $129.00. Amazon this week has a pair of discounts on a few AirPods models, including the AirPods 4 and AirPods Max. You can get the AirPods 4 for $99.00, down from $129.00.
|
|
